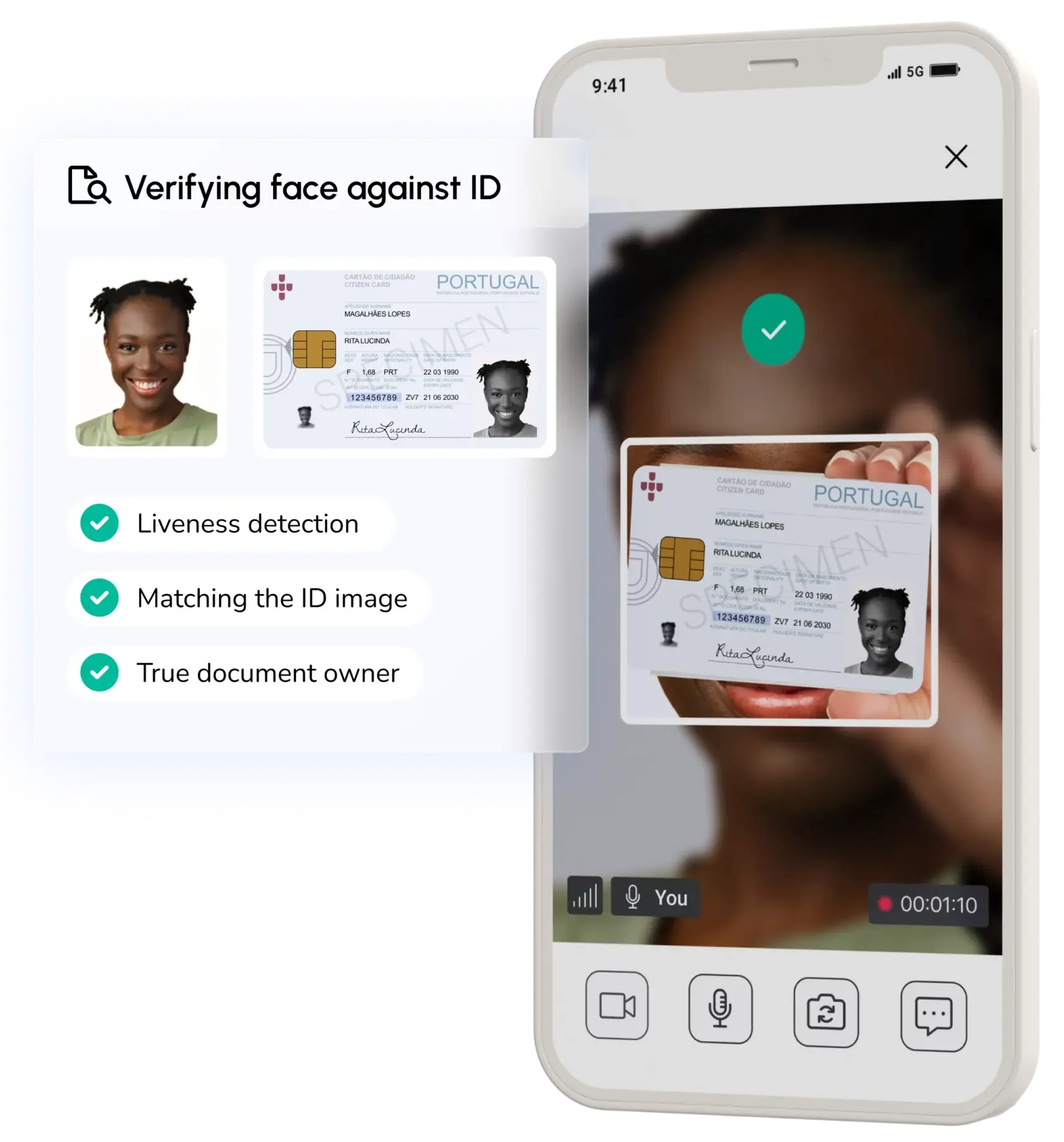
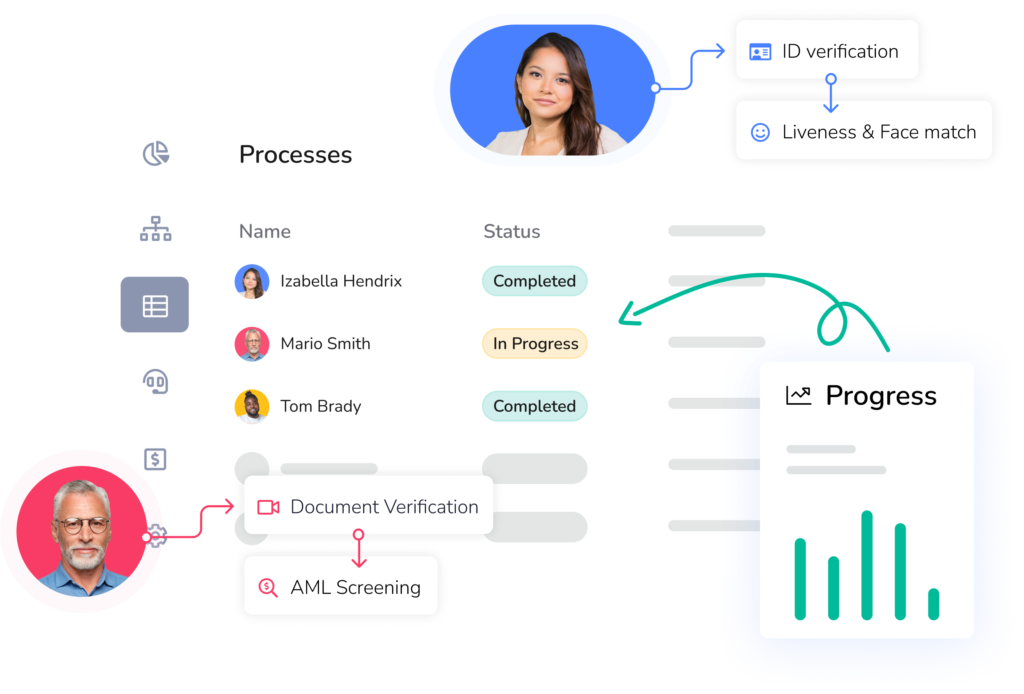
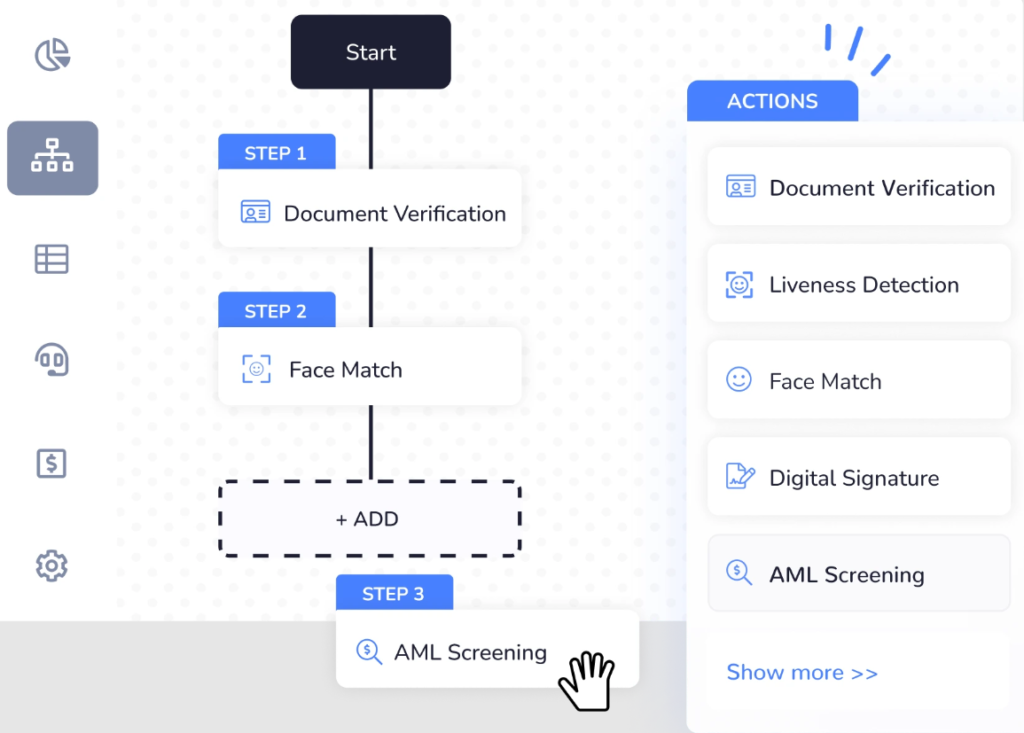
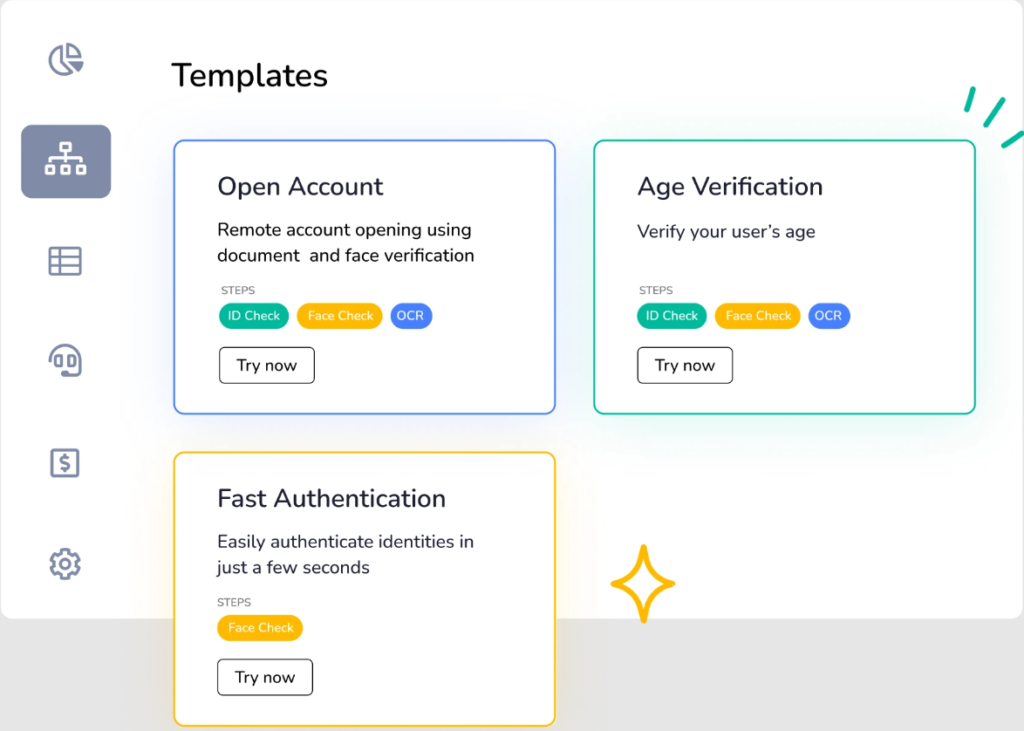
Fully digital identity verification for fast, secure user onboarding.
- ID Document Verification
- ICAO NFC Verification
- Face Liveness
- Face Verification
- Voice Verification
- Voice Anti-Spoofing
- Fingerprints Verification
- Address Verification
- Email Verification
- Mobile Number Verification
- Device Verification
- Handwritten Signature
- Digital Signature
- Video Conference
OUR PROCESS
Trust . Security. Compliance. Fraud Prevention

Data Collection
Gather essential user information through a seamless user interface, optimized for both desktop and mobile experiences

Document Verification
Users can securely upload identity documents such as passports, driving licenses, or utility bills. Our advanced AI-driven technology scans, reads, and verifies these documents in real-time.

Biometric Verification
For added security, we employ cutting-edge facial recognition technology, comparing the user’s live selfie with the photo in their ID document.

Data Cross-Verification
We cross-reference the provided information with trusted databases and data sources globally.

Final Confirmation
Once verified, the user is either granted access or flagged for additional verification, based on the results.

Identity Lifecycle Management
Identity Lifecycle Management (ILM) seamlessly orchestrates the creation, management, and deactivation of identities in a system, ensuring both operational efficiency and security
Key Features
Secure and Compliant
We adhere to global data protection standards, ensuring that user data is handled with the utmost security and respect
User-Friendly
Designed with user experience in mind, making the verification process smooth and hassle-free
Know Your Customer Deeply (eKYC) Simplified
Our eKYC solution streamlines the Know Your Customer process, ensuring that businesses can trust the digital identities of their customers.
eKYC, or Electronic Know Your Customer, is the digital evolution of the traditional KYC process. It leverages technology to verify the identity of users electronically, reducing the need for physical presence or paper documentation.
- Anti-Money-Laundering (AML)
- Customer Due Diligence (CDD)
- Risk Assessment
- Continuous Monitoring
- Address Verification
- Email Risk
- Mobile Number Risk
- Device Risk

A typical KYC program includes three components: a customer identification program (CIP), customer due diligence (CDD), and continuous monitoring
For organizations looking for an identity verification solution that goes beyond CIP and adds value with CDD, it’s essential to ensure that the vendor can connect to relevant data sources, such as checking identities against sanctions lists. The specific requirements for CDD may vary depending on local regulations. Many identity verification vendors and orchestration solutions now offer this connectivity.
If compliance with KYC and AML regulations is the goal, organizations should be cautious when engaging with vendors offering eKYC solutions. It’s crucial to carefully assess each vendor’s capabilities, given the complex and extensive scope of KYC and AML regulation.
Benefits of eKYC
Reduce customer onboarding times from days to mere minutes
Eliminate the need for physical documentation and manual verification processes
Utilize advanced encryption and cybersecurity measures to protect customer data
Stay aligned with international regulatory standards, adjusting to country-specific requirements with ease
Offer customers a seamless, hassle-free onboarding experience, enhancing satisfaction and loyalty
Our system learns and evolves, continuously improving accuracy and fraud detection capabilities
Capable of verifying a wide range of official documents from numerous countries
Seamlessly integrates with existing systems, ensuring minimal disruptions to current operations
Our eKYC Process
Our eKYC solution streamlines the Know Your Customer process, ensuring that businesses can trust the digital identities of their customers
User Registration
Users provide basic information via a streamlined digital interface.
Document Submission
Customers upload digital copies of identity proofs such as passports, national IDs, or driving licenses
Real-time Verification
Our state-of-the-art AI algorithms scan and authenticate documents against global databases
Biometric Confirmation
Incorporate facial recognition or fingerprint scans to match users with their ID documents for an added layer of verification.
Completion
Post-verification, users receive instant notifications regarding their status, expediting the entire onboarding journey
SAFFEGUARDING FINANCIAL INTEGRITY
Anti Money Laundering (AML)
What is Anti Money Laundering?
Anti Money Laundering refers to a set of procedures, laws, and regulations designed to halt the practice of generating income through illegal actions. By implementing effective AML measures, businesses and financial institutions can prevent and combat attempts to launder money and finance terrorism.
Why AML is Crucial:
- Legal Compliance: Adhering to global and regional AML regulations is not only ethical but also mandatory to avoid severe penalties.
- Protecting Reputation: Being associated with money laundering can severely tarnish a business’s reputation, leading to a loss of trust and clientele.
- Operational Integrity: Implementing robust AML measures ensures smoother, more trustworthy operations and partnerships.
- Economic Health: By combating financial crime, businesses contribute to a more stable and healthy global economy.

In the battle against financial crime, we are your first line of defense.
Trust in our state-of-the-art Anti Money Laundering solutions to shield your operations from illicit activities and ensure you stay on the right side of the law
Our AML Solutions

-
Real-time Transaction Monitoring
Scan and analyze transactions in real time to detect suspicious patterns and activities
-
Customer Due Diligence (CDD)
Vet clients thoroughly before onboarding to understand their financial behaviors and backgrounds
-
Enhanced Due Diligence (EDD)
For high-risk clients, we go a step further, diving deep into their financial activities and connections
-
Risk Assessment
Utilize advanced algorithms to assign risk scores to clients, helping businesses tailor their approach
-
Reporting Tools
Seamlessly generate and file necessary reports, such as Suspicious Activity Reports (SARs), in compliance with regulatory bodies
Key Features
Our system is updated with AML regulations from around the world, ensuring compliance regardless of where you operate
Benefit from machine learning and AI-driven insights to enhance detection accuracy and reduce false positives
Our platform is designed with simplicity in mind, ensuring your teams can easily manage and oversee AML operations
Prioritize data protection with top-tier encryption and cybersecurity measures